During a long professional career a lot is supposed to happen along the intricate windings of our mortal life and hence some folklore piles up to be drawn from when telling our grandchildren our adventures.
Once upon a time for example there was a large corporation from the financial sector I was working for for a while. One day the board of directors was confronted with some nasty audit finding, which would prevent them from being compliant to a considerable range of regulations.
As most of the findings were more or less related to IT security, the order to get things right immediately at no costs quickly trickled down the long command chain (well, as I told you, it was a large and prestigious corporation) until it finally pounded the desk of the chief information security officer, also known as CISO in the corporate jargon.
For those, who are not familiar with tribal rites of large corporations I like to reveal a common habit. If new and challenging problems arise on corporate level, which could neither be ignored nor annihilated through a onetime bold & swift strike by top management, but needs long and tedious work on several levels of the hierarchy, we use to assign this task to a new responsibility. By this mechanism special corporate functions like e.g. the Quality Manager (although “quality is everybody’s job”), the Risk Manager (although conscious risk taking is the prime entrepreneurial task of top management) or finally the IT-Security Manager was born.
No one – and this even for good reason – dared to bestow the CISO with sufficient power to really mitigate the root causes of the reported security holes: He might bring the business operations to a grinding halt – secured however. Moreover some responsibilities are loaded on the shoulders of this poor creature, which should not necessarily be included into his role.
Identity & access is quite a good example. Management of identities certainly is not an IT function and even less an IT-security topic. Rather it must be considered as a necessary general organisational infrastructure for any organisation interacting with human (and even non-human) actors. However a functioning Identity Management is a necessary prerequisite to achieve a sufficient security level (as it is for fine grained cost control, process automation, digitalisation …). Even the access part is Janus-headed with one faced toward providing access (e.g. for automation) and one face towards preventing access (hence the IT-security part). Like nearly all business tasks however its implementation eventually needs a heavy IT involvement.
The fatal Todo
So after setting the scene for the drama to unfold, let’s continue with the story. So the CISO was told to deal with the issues and come back with a detailed plan to be presented at the next board meeting (however with 1 week notice period for each intermediate management level). As the CISO was an honest man his proposal was quickly refused by the board as totally unrealistic and amended with the advice to his line manager to straighten out that strange security guy and educate him on how to serve the company interests best.
“Ok folks hear the news. The board is not amused. The situation is serious. It’s not the right time to present your wish list, of what you always wanted to address. They are not stupid up there. They know all these tricks for long. So, no gold plating, don’t’ try to boil the ocean – just the security issues and nothing else.”
Poor CISO, he desperately tried to explain, that IT-security is not an add-on, but that it rather is deeply rooted in the IT processes and even more in the whole organisational framework, which he was not the least mandated to address.
Listen to his plea:
Look, Compliance is just the result of a long-term effort. That’s the bad news. The good news is that after investing all this effort it comes as a by-product. I am tempted to borrow the quote from Philip Crosby: (quality is free)
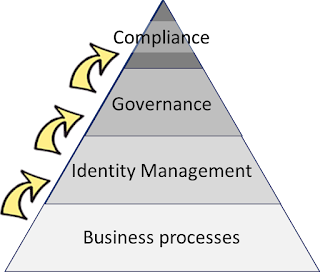 |
| The compliance pyramid |
1. Identity & Access depends on Business
Representing an organisational infrastructure layer, Identity & Access processes depend on a sufficient maturity of the of underlying Business processes, which they are meant to support. A major part of these business processes is represented by the workforce management processes (aka Human Resources).
Roles are the business
To get a grip on the inherent complexity of a large organisation, it has become commonly accepted practice to express a person’s task in roles (if they are to be considered as sufficiently static) or business rules (in a more dynamic environment). They jointly with some other dimensions or constraints like location, amount authorisation, contract type, organisational Unit and the like determine the necessary and hence maximum access to corporate resources. These business roles however as well as business rules have - the naming gives a strong indication already - to be defined in business terms by business literate staff. Only after that is done they should be underpinned by low level permissions (aka permissions, entitlements, privileges, access rights, …). Ideally the job description is linked to a set of business roles / rules already.
Workforce Management Policies
Moreover policies should be in place to provide the Identity & Access domain with the necessary guidance. Policies with some influence on Identity & Access may pertain the scope of the workforce (e.g. Contractors, trainees, apprentices, interns, temp. staff included?), automation of time & attendance tracking, automation of employee/manager self-service functions, deputy procedures in case of planned / unplanned absence, formalisation of a flexible, remote and mobile working strategy, retention times for personal information / digital identities, and finally the standardisation of processes & policies itself.
When taking digitisation seriously, the processes of the identity & Access should be automated in all standard cases – relying however on timely and meaningful triggers fired by the workforce management.
So there is a lot of solid ground which can and should be provided by the business side to support a rock solid Identity & Access layer. If workforce management is however only not rigorously enough defined and only loosely coupled to Identity & Access, no one should be surprised if the latter remains shaky and unreliable.
On the other side – the assets
Let’s remember. The Access part of Identity & Access is about the relationship of 2 major objects: the digital identity (most often representing a person) and the asset to be protected. So, not surprisingly, not just the person has to be well known and properly embedded in workforce processes – the assets have to be too. So first there must be a registry or repository of all assets. The assets documented therein must be sufficiently characterised. A responsible owner has to be assigned and – most importantly – the asset must be assigned to a sensitivity class after undergoing a thorough sensitivity analysis.
The enterprise model
As I mentioned above, roles are the business and it is necessary to express a person’s task in roles. But where do roles come from? They are not invented on the fly during the recuting process. Nor do they emerge somewhere form thin air. They are to be populated by business functions from an enterprise model. Well and this should better be handy to do so. In cases when such models exist, most often they are functional enterprise models, hierarchically structured and named canonically and via aliases. Canonical naming is required for methodological rigour and to easily spot commonalities, aliases for the sake of comforting business by mirroring their folkloric designations from their business as usual. Functional model are often well suited, as regulations requiring e.g. Segregation of Duties (SoD) are overwhelmingly expressed in functions to be assigned to different actors. Even more helpful would be the use of an object oriented enterprise model.
2. The Management layer feeds Governance
Governance is defined as giving direction to and exerting oversight over the underlying Management processes in the focus area.
Direction
We talked about giving direction already. Good governance here has to craft and publish a domain strategy, closely in line with the overall enterprise strategy. Its results should be fed into policies for the business as usual or action for the defined change activities. The role of corporate policies can’t be overemphasised here.
Oversight
It is so obvious that knowing what’s going on in the domain of your responsibility, is a key requisite of all governance efforts – and it as obviously so difficult to achieve. The mechanisms how to exert oversight, are already laid out in a bit more detail elsewhere.
For the sake of clarity and to provide a good fit to the next – the compliance layer – it is advisable to compile a list of control objectives and implement them in one or more management controls each. Even in the absence of compliance requirements good guidance abound in several standardisation or management models like CoBIT5, ISO 27000 series and more.
It is not to concealed here, that gaining the necessary overview on may require a massive involvement of technology use, like advanced analytics or even big data.
3. Governance feeds Compliance
As implied by the illustration with its pyramidal appearance, this chapter should even be shorter than the one before, which in turn was shorter than the first one. The major amount of work indeed should have been done in the lower levels, so that the compliance layer should become a cheap one.
This doesn’t mean that no more work is involved. As I mentioned here before, Thomson Reuters once counted a mere number of ~100 minor or major regulatory changes per day to be taken into account, most of them in the financial sector, many of them IT-security related. This sheer number, which is even expected to rise, justifies assigning the responsibility of watching out for new / changed regulations, assessing their relevance, operationalising them as controls, matching with existing ones and if necessary, initiating change activities to get them implemented, to an own function.
So
once we have done all our homework, which are anyway elements of good conduct,
compliance does not need to be artfully crafted. Rather it just bubbles up from
the layers below – nearly for free.
But you can’t fool a strong leader
Hours later after patiently waiting and pretending to carefully listen to the CISO’s lengthy, while still not exhausting, elaboration.
“Dear colleague, I really don’t understand, what you are saying. First you presented a huge bill to us, containing lots of items; we all would have to pay for dearly, besides that you threatened us with a huge effort and a yearlong duration. Now you tell me it comes for free. Isn’t it a bit strange – to say the least. I don’t want to repeat myself. Hopefully you listened carefully to the message from above. I strongly recommend: Just the compliance issues – and just do it!”
Having said that the line manager left in a good mood. Didn’t he just demonstrate strong leadership, after all?
You like to know, how the story ended, if it had a happy end? Well, I think you may not really want to know that. You most probably can already quite easily sense it ...
So this could become one of the often repeated talks form the past. However as I am not blessed with grandchildren yet, the public fell victim of my insatiable talkativeness.